Windows Bursting on AWS and Azure
Requirements for bursting Windows cloud nodes.
OS Image Name
When creating the OS image, the name of the image must contain the term "windows" (case insensitive). For example:On AWS, the AMI Name should look something like this Windows_Server-2012-R2_RTM-English-64Bit-Base-2019.11.13
On Azure, the Image Name should look something like Windows Server 2012 R2 Datacenter.
Inbound Security Rule for RDP
Secondly, an inbound rule to open the port 3389 must be added to the AWS security group or the Azure network security group that is associated with the cloud provider virtual network. This allows a connection to be made to the Windows VM via RDP so that the PBS MoM can be installed.
For more information see AWS: Authorizing Inbound Traffic for Your Windows Instances and Azure: Cannot connect remotely to a VM because RDP port is not enabled in NSG.
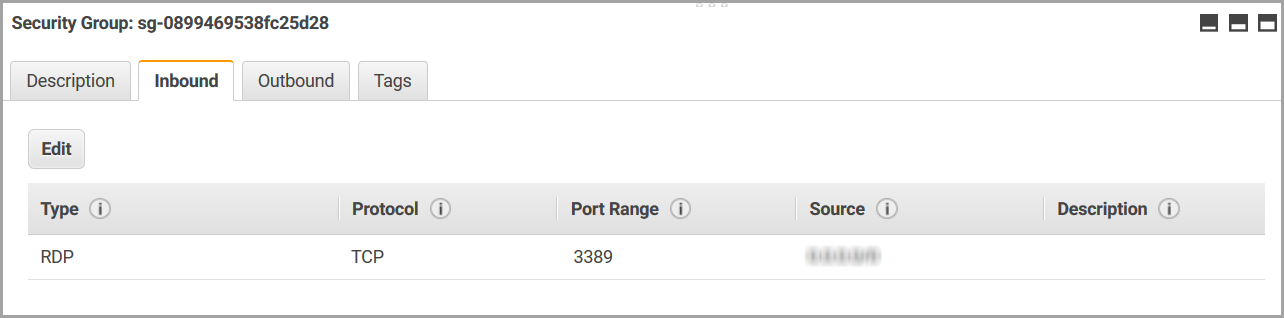
Figure 1. AWS Inbound Security Rule for RDP
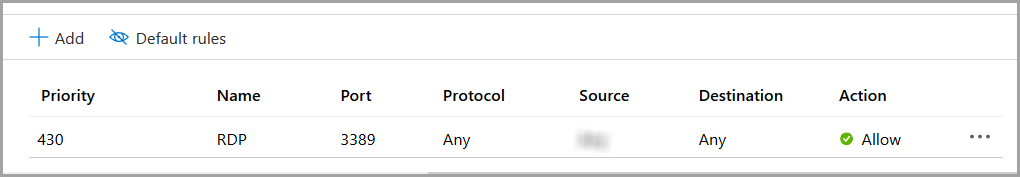
Figure 2. Azure Inbound Security Rule for RDP
Startup Script
The cloud node startup script must use a PowerShell script. For more information see PowerShell Scripting. The below PowerShell script example generates a file in C:\Windows\Temp:
<powershell>
$file = $env:SystemRoot + "\Temp\" + (Get-Date).ToString("MM-dd-yy-hh-mm")
New-Item $file -ItemType file
</powershell>